More intelligence.
Less confusion.
E2 - Everything Everywhere
Imagine a database that ingests over unique threat information sources and feeds in real-time; knowledge as it happens!
It has the ability to see
- the latest and greatest intelligence as it is created
- multiple sources for enrichments
- outdated and benign threats
- threat duplication and overlaps
- emerging threats
- and a multiplicity of insights.
This unparalleled visibility is a core foundational technology that is required to cross-compare and correlate CTI to establish efficacy measurements and an individualized curation of a CTI portfolio. This convergence of real-time knowledge is the next logical step in threat intelligence and fundamental to our offering. The statistics are a real-time display of our visibility that powers our curation capabilities.
Click here for a current list of threat feeds* – if you don't see one that your company is already using, simply provide us the license key* to do the analytics.
* Sign up required
New IOCs (last 24h)
14 days trend
14 days trend
14 days trend
Noise in Signals
14 days trend
Garbage in, Garbage out? Not with Ticura
Our AI turns raw data into strategic intelligence, automatically, in real time, and with unmatched precision. Threat intelligence is only as good as the data behind it. But even the best raw data is useless without intelligent processing. That’s where Ticura excels:
- AI-powered data refinement: sources (including dark web, open source, and premium feeds) are continuously analyzed, validated, and enriched by a self-learning AI that detects errors, eliminates duplicates, and adds context before the data ever reaches your systems.
- Predictive Quality Control: Our algorithms anticipate which indicators will matter and proactively filter out noise before it wastes your analysts’ time.
- From Big Data to Smart Data: Using machine learning and natural language processing (NLP), we transform raw data into actionable insights with an accuracy no manual process can match.
The result? No ‘garbage out’, just intelligence that actually moves your security forward.
A multi-tenant solution, ticura improves ROI for everyone
In real-time, Ticura collects threat intelligence from more than free and commercial sources. Then leveraging its proprietary engine, data science, and machine learning we enrich, normalize, and categorize the data to compare with your CTI and security event logs to recommend an optimal combination of CTI.
Ticura then seamlessly delivers the optimal CTI sources to your security infrastructure with continuous feedback and refinement.
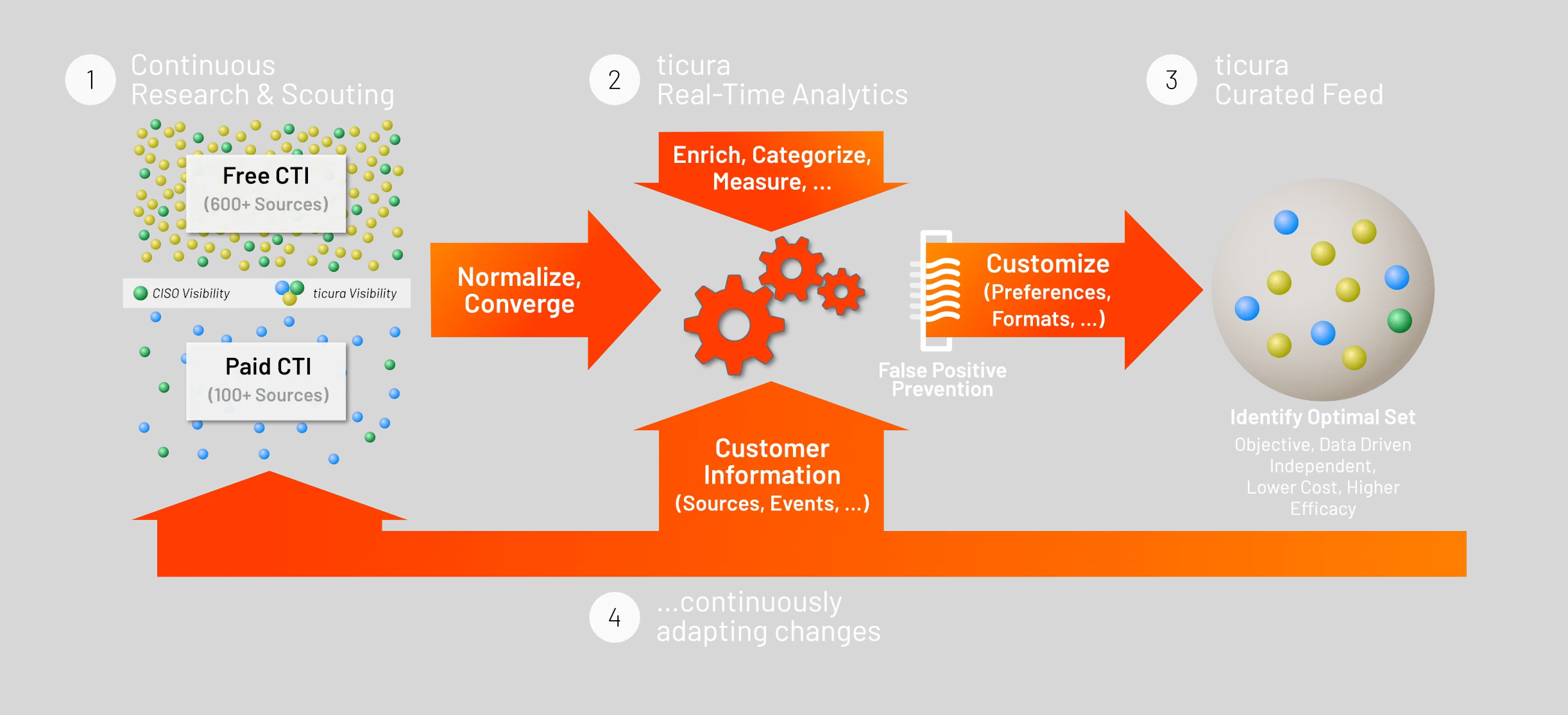
Real-time prioritization by measuring the relative effectiveness of individual threat intelligence sources removes the need for analysts to choose which data sources are important or not and enables you to eliminate costs associated with redundant or ineffective feeds.
With Ticura:
- Confidently select the optimal set of threat feeds and eliminate superfluous subscription fees.
- Minimize false positives alerts and free up resources to proactively protect against evolving threats.
- Significantly expand your global intelligence footprint while focusing on alerts that matter.
- No training, overhead or changes to your application environment required.
More Signal. Less Noise.
The ticura solution is continuously conducting real-time analysis of more than 1.5 Billion IOCs per day from more than sources to validate and assess the accuracy and validity of the indicators.
By applying numerous methods like DNS Analytics, Internet Rank Analytics, Whois lookups and many more indicators are now assigned to categories like CDN, ISP, known sinkholes, parking or offline domains, which enables the easiest, most effective, industry leading false positive prevention perspective.
With these insights ticura allows clients to possess a distinctive advantage as it relates to interpreting and consuming CTI inputs. This processing enables a near real-time consumption of the information to identify the most recent and late-breaking changes to the global IOC environment with a 4% change each cycle, and additionally results in roughly 1 Million new, first-seen, IOCs per day.
Single pane of glass management and insight.
With continuous research, enrichment, normalization, and aggregation of all information sources in the recommended portfolio we provide a single pane of glass for the research of analysts, threat hunters and incident responders.
Put an end to the hassle of working with a multitude of portals from different vendors. No more working with islands of intelligence.
Seamless integration into existing infrastructure
-
Dynamic, global repository
sources today, continuously growing
-
Lossless normalization
Continuously monitored and improved
-
Correlation, Deduplication
Lossless across all sources, preserving metainfo for full insights
-
Enrichment
Continuously growing from 100s of sources and methods
-
Dynamic Categorization
Based on ML, features and rules
-
Measure relevance and efficiency
All sources, based on customer preferences, events
-
Curate optimal source set
Based on efficiency and relevance
-
Intelligent False Alert Prevention
Category based, customizable, optimized
-
Optimized Export
Optimized format for each customer
-
Existing Infrastructure
Optimized for insights, integrate with nearly no effort